What do network gadgets actually do?
Network devices are components that enable communication between services and the endpoints that use them. In other words, they're network connectors that allow devices to communicate with one another. Enabling communication refers to anything that aids data transmission from source to destination, such as a network switch transmitting frames between two LAN devices.Communication can be restricted by stopping it from taking place. Two examples are a firewall rule that limits traffic from TCP port 23 and a VLAN that divides broadcast domains.
We don't use the term "hardware" to describe network devices.This is due to the virtualization or software-based nature of many network operations and appliances. You can use a virtual appliance to operate as a router, network switch, or firewall, for example.
A crash course in the OSI model and data types
Understanding the levels of the OSI (Open Systems Interconnection) architecture is one of the greatest ways to comprehend the purpose of various network devices. The OSI model is a conceptual model that describes how data moves across and within networks.
These two components of the OSI model will help you understand how different network devices work:
NAS (Network attached storage)
A NAS is a server that just stores files. A NAS offers a central storage point for a LAN that may be utilised for things like shared file access and user data backups. NAS devices are an inexpensive and straightforward approach to deliver network storage. As NASes continue to offer more complex capabilities suitable to small and mid-sized workplaces, the distinctions between NASes are starting to offer more extensive capability for small and mid-sized businesses.
Balancer of loads
Client connections are distributed across numerous servers via load balancers. Load balancers, like firewalls, come in a variety of software and hardware configurations. Load balancers typically function at Layer 4 or Layer 7 (filtering traffic based on TCP or UDP) (filtering based on HTTP or DNS traffic). The following are some examples of load balancing strategies:
• Round-robin: Simply sends requests in a cycle to each server.
• Least connections: A type of load balancing in which connections are sent to the server with the fewest connections first.
• Weighted least connections: Similar to weighted round-robin, weighted least connections assigns "weights" to servers that impact load.
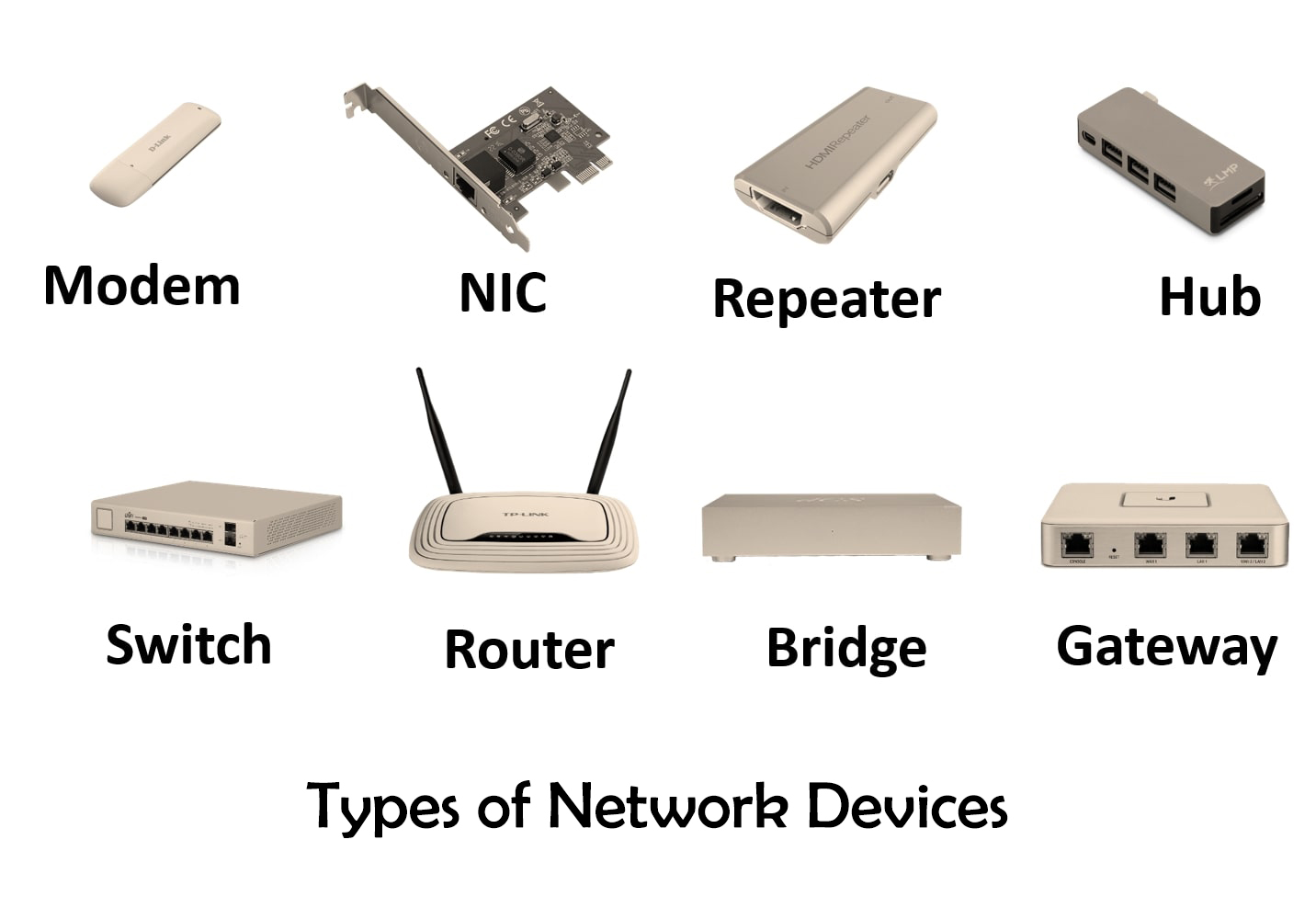
Modem
By the traditional definition, a modem device that modulates and demodulates a signal to and from analog and digital. In the days of dial-up internet, modems were used to connect local computer networks to analog telephone lines for internet access.
Hub
A hub is a basic Ethernet repeater that works at Layer 1, allowing several devices to join to the same Ethernet network. A hub, unlike a switch, does not split collision domains, which means that all ports on a network hub get the same traffic. As a result, hubs, like WiFi repeaters, can generate significant traffic congestion.
Hubs can cause severe network congestion by rebroadcasting traffic to all ports. If you need a hub, consider an unmanaged switch instead, which will split up collision domains.
Bridge
Network bridges were traditionally Layer two devices with only two ports. They, like switches, broke up collision domains and, when compared to hubs, might minimise network congestion by dividing the network into many collision domains.
However, depending on the context, the term "bridge" can now indicate a lot more than that traditional connotation. Other meanings of the phrase network bridge include:
• A network switch • A device that can join VLANs at Layer 2
• A device that can connect two networks utilising various types of connections, such as a WLAN to a conventional LAN.
Firewalls
Firewalls can be software, hardware, or a combination of both. Additionally, the rules firewalls use can be based on something straightforward like ports and IP addresses or use heuristics to identify malicious behavior.
These firewalls operate at Layer 3 and Layer 4 and use rules to decide whether traffic should be dropped or forwarded depending on IP addresses, port numbers, and packet types. One of the benefits of this basic method of traffic inspection is that it has no effect on network speed.



Comments
Post a Comment